Malware rarely needs cutting-edge exploits to succeed. More often, attackers rely on something far simpler - our trust. A recent campaign shows how malicious advertising and look-alike websites are being used to distribute Oyster malware under the guise of Microsoft Teams installers.
How the Attack Works
Researchers observed attackers using Search Engine Optimisation (SEO) poisoning and paid ads to lure users searching for “Teams download.” Victims were redirected to fraudulent domains such as teams-install[.]top which closely mimic legitimate Microsoft download pages. On these sites, users were offered a trojanised installer named MSTeamsSetup.exe (the same name as Microsoft’s genuine installer). Once executed, the installer dropped a malicious Dynamic Link Library (DLL) called CaptureService.dll into the user’s roaming profile. It also created a scheduled task set to trigger every 11 minutes – ensuring the backdoor stayed active even after reboots. This behaviour is consistent with Oyster (also known as Broomstick or CleanUpLoader), a backdoor used since 2023 to gain initial access into corporate environments.
Why Oyster Matters
Oyster may not make headlines like ransomware but once installed, the malware allows:
- Remote command execution
- File uploads/downloads
- Deployment of additional payloads
Security teams have linked Oyster to campaigns that later delivered ransomware such as Rhysida. Its effectiveness lies in its simplicity – it exploits trust in familiar tools and legitimate-looking files.
Visualising the Attack Chain
Here’s a simplified diagram showing how the campaign unfolds:
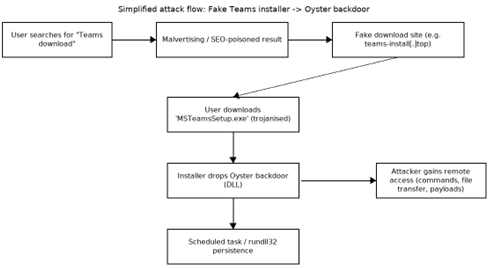
- User searches for “Teams download”
- Malicious ad / SEO-poisoned result appears
- Fake website serves trojanised installer
- Installer drops Oyster DLL backdoor
- Scheduled task ensures persistence
- Attacker gains remote access and control
What Organisations Should Do
This campaign reinforces some fundamentals of cyber hygiene:
- Never trust ads or top search results for downloads – go directly to the vendor’s official site.
- Verify installers – check file names, digital certificate issuers, and whether they match expectations.
- Hunt for persistence indicators – anomalous scheduled tasks (e.g. “CaptureService”) are red flags.
- Defence in depth – combine web filtering, endpoint detection, application controls, and user awareness training.
Even experienced IT staff can be caught out by a familiar brand and a trusted-looking certificate. The adversaries know this -and build their attacks around it.
Appendix: Quick Triage Checklist
If you suspect Oyster activity, here are some fast checks your IT or SOC team can run:
- File system checks
- Look for suspicious DLLs in user roaming profiles, especially CaptureService.dll.
- Check Downloads folders for MSTeamsSetup.exe or MSTeamsSetup.msi not signed by Microsoft.
- Scheduled tasks
- Run schtasks /query /fo LIST /v and look for unknown tasks (e.g. “CaptureService”) running every 10–15 minutes.
- Pay attention to tasks launching rundll32.exe.
- Process monitoring
- Identify abnormal rundll32 activity, especially when loading DLLs from user profiles.
- Correlate with parent processes like recently installed “setup.exe” or “MSTeamsSetup.exe.”
- Network indicators
- Monitor for unusual outbound connections shortly after Teams installation.
- Compare against threat intelligence IOCs (Indicators of Compromise) published for Oyster.
- Containment steps
- Immediately isolate affected endpoints from the network.
- Collect forensic artefacts before remediation.
- Reset potentially exposed credentials.
This checklist isn’t exhaustive but can help SOCs spot Oyster before attackers move deeper into the environment.
References
- BleepingComputer – Fake Microsoft Teams installers push Oyster malware via malvertising (Sept 2025)
- Blackpoint SOC analysis, 2025
- Threat feeds including ThreatFox (IOC listings for Oyster/Broomstick)