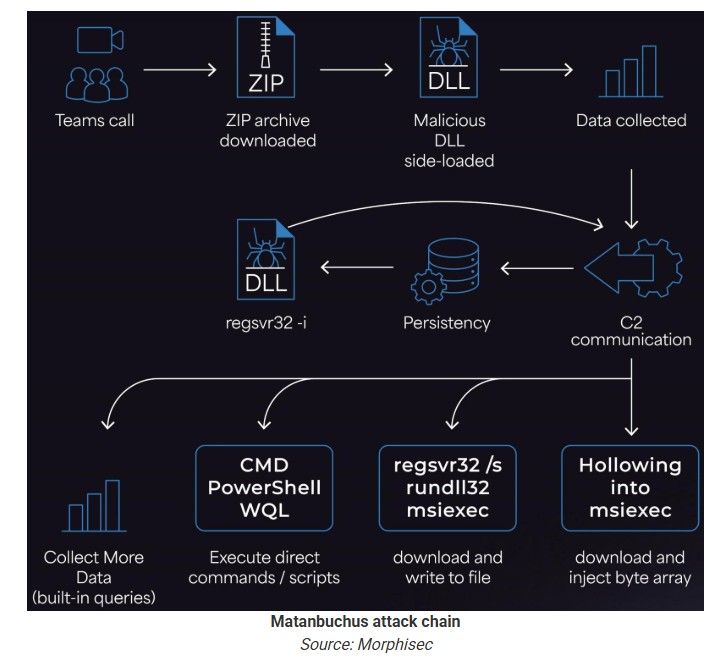
A new attack method is using Microsoft Teams voice calls to deliver Matanbuchus 3.0, a malware loader capable of stealthy in-memory execution and post-exploitation control.
This isn’t a vulnerability – it’s an abuse of trust. Threat actors pose as IT support, call targets via Teams, and convince them to launch Windows Quick Assist.
The result?
Full access, malware deployed, and monitoring bypassed.
What makes this threat particularly dangerous:
🔸 Real-time social engineering, not phishing emails
🔸 Abuse of legitimate tools like Quick Assist & PowerShell
🔸 DLL sideloading and encrypted C2 to evade detection
🔸 Capabilities to load EXEs, DLLs, shellcode, and persist quietly
What can security and IT teams do now?
🔍 Review Teams external access settings—limit or restrict as needed
🚫 Disable Quick Assist on endpoints unless explicitly required
📊 Monitor PowerShell activity and remote sessions closely
👥 Train users to verify all unsolicited support requests
📣 Raise internal awareness—this is a shift in attack technique, not just tooling
In conclusion
This is a critical example of how attackers are pivoting from static payloads to interactive trust abuse. Security postures must adapt accordingly – especially where collaboration tools and native OS features intersect.
Matanbuchus attack chain